Delegated Authentication Single Sign-On in Salesforce. How to achieve this with Okta?
Delegated Authentication Single Sign-On -
- We can configure our Salesforce org with any authentication method of our choice using this feature of salesforce.
- We can integrate with the LDAP server - Lightweight Directory Access Protocol or authenticate with the access token rather with the password.
- We can also manage authentication at the permission level which gives us more flexibility.
- With the above feature, we can set delegated authentication for particular users rest will use their salesforce credentials for login.
- If user tries to login through online or API, Salesforce checks permission settings and access settings after validating the username.
- If user has enabled the Single Sign On permission setting then salesforce doesn't validates the login credentials. Rather it makes an web service call to org for validating the login credentials.
- When above permission setting is enabled then salesforce no longer manages the password policies for example - password must be of required minimum length.
- Then delegated authentication comes into action, the endpoint's service enforces the policies for password.
- Note - In this case salesforce doesn't store or view the password. It dispose the password when process get completed.
- With this delegated authentication feature, user will experience a delay than normal while logging.
How to achieve Delegated Authentication with Okta's satandard apps?
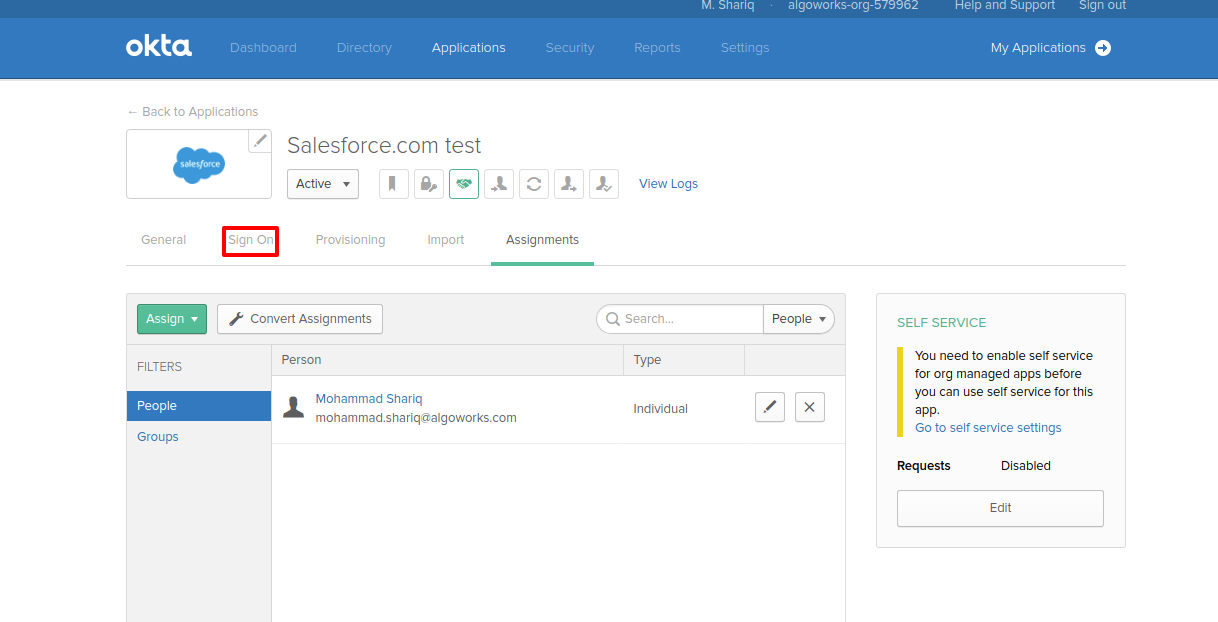
- Open your Okta's standard app detail page and click on Sign On tab.
- Click on View Setup Instructions button and go to Delegated Authentication section of that page.
- Copy the URL under Delegated Gateway URL heading.
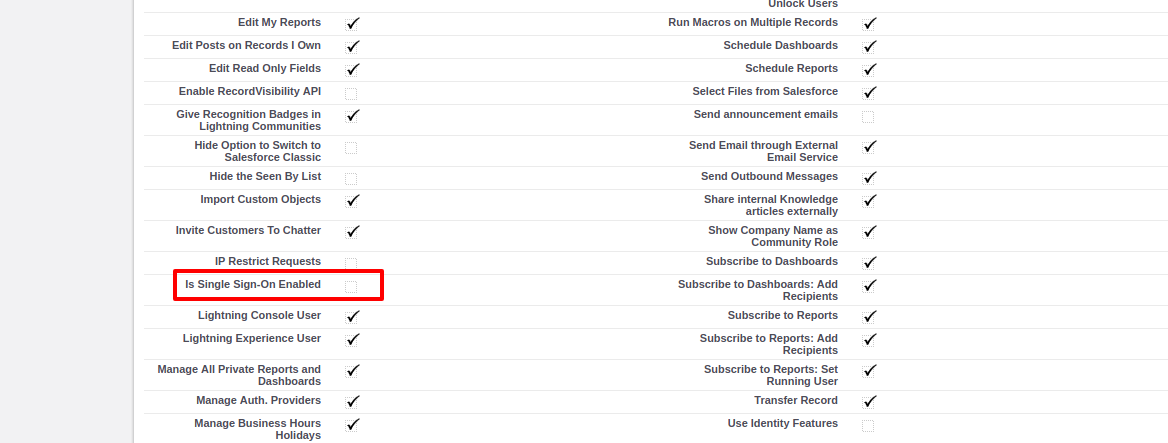
- Now go to your salesforce org's profile detail page and select the profile you want to use for delegate authentication, for now I am doing with my System Admin profile.
- This will open your profile detail page, go to Is Single Sign-On Enabled checkbox and enable it.
- So now System admin users will never able to login through normal salesforce process.
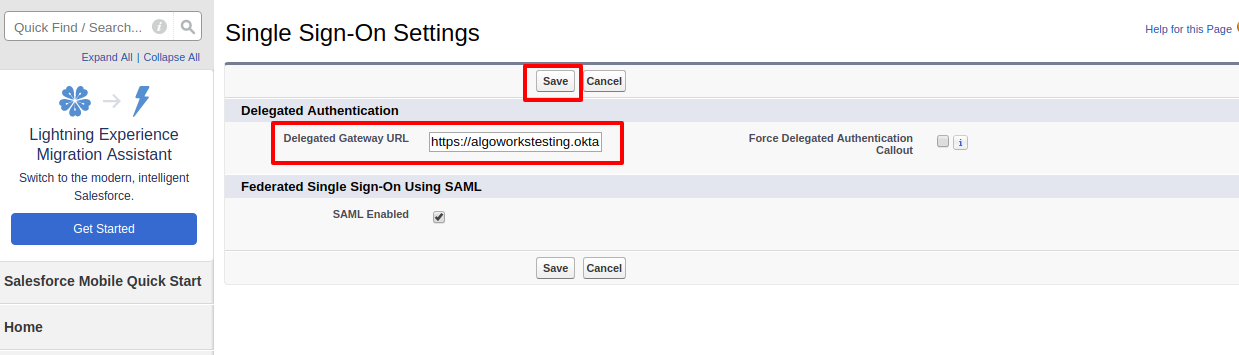
- Now go to Single Sign On settings in your org, and click Edit button. Paste the URL you have copied earlier in Delegated Gateway URL.
- Click Save.
- System Administrator users will only able to login through that Okta's app gateway endpoint, now Okta manages the password policies for those salesforce users.